AWS IoT Core SSH: A Comprehensive Guide To Secure Remote Access
In today's interconnected world, AWS IoT Core SSH has become an essential solution for securely managing devices and applications in the Internet of Things (IoT) ecosystem. With the rise of smart devices and industrial automation, ensuring secure communication between devices and cloud platforms is crucial. AWS IoT Core provides a robust framework for connecting IoT devices, and integrating SSH (Secure Shell) adds an extra layer of security for remote access and management.
AWS IoT Core SSH allows developers and system administrators to remotely connect to IoT devices, enabling them to troubleshoot, configure, and maintain these devices efficiently. This capability is particularly important for organizations deploying IoT solutions across geographically dispersed locations, where physical access to devices may not always be feasible.
This article will explore the integration of SSH with AWS IoT Core, highlighting its benefits, challenges, and best practices. Whether you're a developer, IT professional, or decision-maker, this guide will equip you with the knowledge to implement secure remote access for your IoT infrastructure.
Read also:The Comprehensive Guide To The Meaning Of M
Table of Contents
- Introduction to AWS IoT Core SSH
- Overview of AWS IoT Core
- Benefits of Using SSH with AWS IoT Core
- AWS IoT Core SSH Architecture
- Implementation Steps for AWS IoT Core SSH
- Security Best Practices for AWS IoT Core SSH
- Troubleshooting Common Issues
- Scaling AWS IoT Core SSH Solutions
- Real-World Use Cases
- Future of AWS IoT Core SSH
Introduction to AWS IoT Core SSH
AWS IoT Core SSH represents a powerful combination of Amazon Web Services' IoT platform and the Secure Shell protocol. AWS IoT Core serves as the backbone for managing IoT devices, enabling secure and reliable communication between devices and the cloud. By integrating SSH, users can establish secure remote connections to IoT devices, enhancing operational efficiency and device management.
SSH is widely regarded as one of the most secure methods for remote access, providing encryption for data in transit and authentication mechanisms to ensure only authorized users can connect to devices. This makes it an ideal solution for IoT deployments where sensitive data is transmitted and device security is paramount.
The integration of SSH with AWS IoT Core addresses critical challenges in IoT management, such as secure device access, data protection, and scalability. This section will delve deeper into the technical aspects of AWS IoT Core SSH and its role in modern IoT ecosystems.
Overview of AWS IoT Core
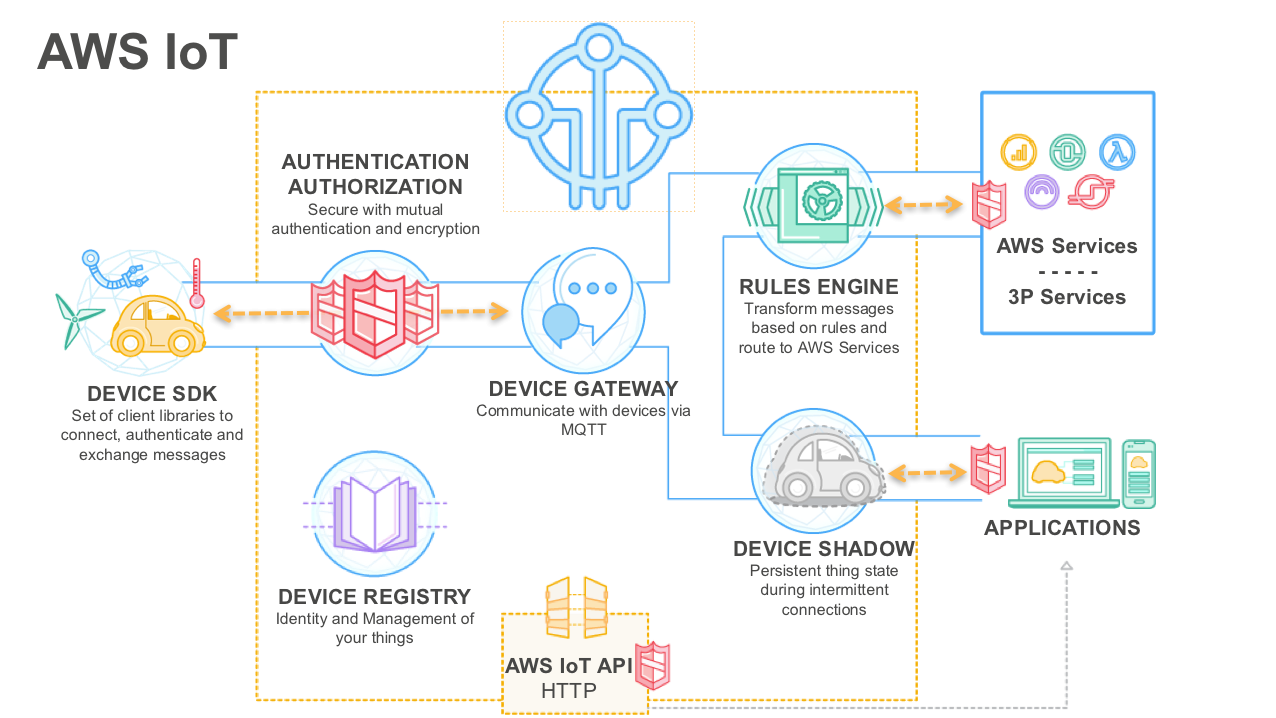
AWS IoT Core is a managed cloud service designed to handle billions of devices and trillions of messages. It acts as a bridge between IoT devices and cloud applications, enabling seamless communication and data exchange. AWS IoT Core supports various protocols, including MQTT, HTTP, and WebSocket, ensuring compatibility with a wide range of devices and use cases.
Key Features of AWS IoT Core
- Device Management: Register, monitor, and manage IoT devices at scale.
- Rules Engine: Process and route IoT data to other AWS services for further analysis or action.
- Device Shadow: Maintain a virtual representation of device state, allowing applications to interact with devices even when they're offline.
- Security: Implement robust security measures, including device authentication, encryption, and access control.
AWS IoT Core's ability to integrate with other AWS services, such as AWS Lambda and Amazon S3, makes it a versatile platform for building comprehensive IoT solutions. By incorporating SSH, AWS IoT Core extends its capabilities to include secure remote device management, addressing a critical need in the IoT landscape.
Benefits of Using SSH with AWS IoT Core
Integrating SSH with AWS IoT Core offers numerous advantages for organizations deploying IoT solutions. Below are some key benefits:
Read also:Dangerous Zodiac Signs Understanding The Bold And Fearless Traits
Enhanced Security
SSH provides strong encryption and authentication mechanisms, ensuring secure communication between devices and cloud platforms. This is particularly important for IoT deployments involving sensitive data or critical infrastructure.
Remote Device Management
With SSH, users can remotely access and manage IoT devices, streamlining operations and reducing the need for physical interventions. This capability is especially valuable for large-scale IoT deployments where devices are spread across multiple locations.
Improved Efficiency
SSH enables efficient troubleshooting and configuration of IoT devices, minimizing downtime and maximizing operational efficiency. System administrators can quickly diagnose and resolve issues without the need for on-site visits.
AWS IoT Core SSH Architecture
The architecture of AWS IoT Core SSH involves several components working together to facilitate secure remote access to IoT devices. Below is an overview of the key elements:
- AWS IoT Core: Acts as the central hub for device communication and management.
- SSH Client: Installed on the user's local machine, allowing them to initiate secure connections to IoT devices.
- SSH Server: Running on the IoT device, enabling it to accept incoming SSH connections.
- Security Mechanisms: Includes authentication, encryption, and access control to ensure secure communication.
This architecture ensures that all communication between the user and the IoT device is encrypted and authenticated, protecting against unauthorized access and data breaches.
Implementation Steps for AWS IoT Core SSH
Implementing AWS IoT Core SSH involves several steps to ensure a secure and efficient setup. Below is a step-by-step guide:
1. Set Up AWS IoT Core
Create an AWS account and set up AWS IoT Core. Register your IoT devices and configure the necessary settings for communication.
2. Install SSH Server on Devices
Install an SSH server on each IoT device you wish to manage remotely. Ensure the server is configured securely, with strong authentication and encryption settings.
3. Configure Security Settings
Set up authentication mechanisms, such as public-key authentication, and define access control policies to restrict who can connect to the devices.
4. Test the Connection
Use an SSH client to establish a connection to the IoT device and verify that the setup is functioning correctly. Test various scenarios to ensure the system is robust and secure.
Security Best Practices for AWS IoT Core SSH
Security is paramount when implementing AWS IoT Core SSH. Below are some best practices to ensure a secure setup:
- Use strong passwords and enable two-factor authentication (2FA) wherever possible.
- Regularly update SSH servers and clients to patch vulnerabilities and improve security.
- Monitor SSH connections and log activities to detect and respond to suspicious behavior.
- Limit access to SSH ports and restrict connections to trusted IP addresses.
By adhering to these best practices, organizations can minimize the risk of security breaches and ensure the integrity of their IoT deployments.
Troubleshooting Common Issues
While AWS IoT Core SSH is a powerful solution, users may encounter issues during setup or operation. Below are some common problems and their solutions:
Connection Issues
If you're unable to establish an SSH connection, verify that the SSH server is running on the device and that the necessary ports are open. Check firewall settings and ensure there are no network restrictions blocking the connection.
Authentication Failures
Authentication issues can arise due to incorrect credentials or misconfigured settings. Double-check your authentication methods and ensure all configurations are correct.
Performance Problems
If the connection is slow or unstable, consider optimizing your network settings and ensuring the device has sufficient resources to handle SSH connections.
Scaling AWS IoT Core SSH Solutions
As IoT deployments grow in size and complexity, scaling AWS IoT Core SSH solutions becomes crucial. Below are some strategies for scaling:
Load Balancing
Implement load balancing to distribute SSH connections across multiple devices, ensuring optimal performance and reliability.
Automated Management
Use automation tools to streamline device management and reduce the burden on IT staff. This can include automating configuration updates, security patches, and monitoring tasks.
Scalable Infrastructure
Design your infrastructure to accommodate growth, using scalable AWS services and architectures to support increasing numbers of devices and connections.
Real-World Use Cases
AWS IoT Core SSH has been successfully implemented in various industries, addressing diverse challenges and requirements. Below are some real-world use cases:
Smart Manufacturing
In the manufacturing sector, AWS IoT Core SSH enables remote monitoring and maintenance of industrial equipment, reducing downtime and improving efficiency.
Smart Cities
For smart city initiatives, SSH integration with AWS IoT Core allows for secure management of infrastructure components, such as traffic lights and environmental sensors.
Healthcare
In healthcare, AWS IoT Core SSH ensures secure communication between medical devices and cloud platforms, safeguarding sensitive patient data and enabling remote diagnostics.
Future of AWS IoT Core SSH
The future of AWS IoT Core SSH looks promising, with ongoing advancements in IoT technology and security protocols. As more devices become connected, the demand for secure remote access solutions will continue to grow. AWS is committed to enhancing its IoT offerings, ensuring they meet the evolving needs of businesses and industries worldwide.
In the coming years, we can expect to see improvements in performance, scalability, and security, as well as the integration of emerging technologies such as artificial intelligence and machine learning to further enhance IoT capabilities.
Conclusion
AWS IoT Core SSH provides a powerful and secure solution for managing IoT devices remotely. By integrating SSH with AWS IoT Core, organizations can ensure the integrity and security of their IoT deployments while improving operational efficiency. This article has covered the key aspects of AWS IoT Core SSH, including its benefits, architecture, implementation steps, and best practices.
We encourage readers to explore AWS IoT Core SSH further and consider implementing it in their IoT projects. For more information, please refer to the official AWS documentation and other trusted resources. Don't forget to share your thoughts and experiences in the comments section, and explore other articles on our site for more insights into IoT and cloud technologies.