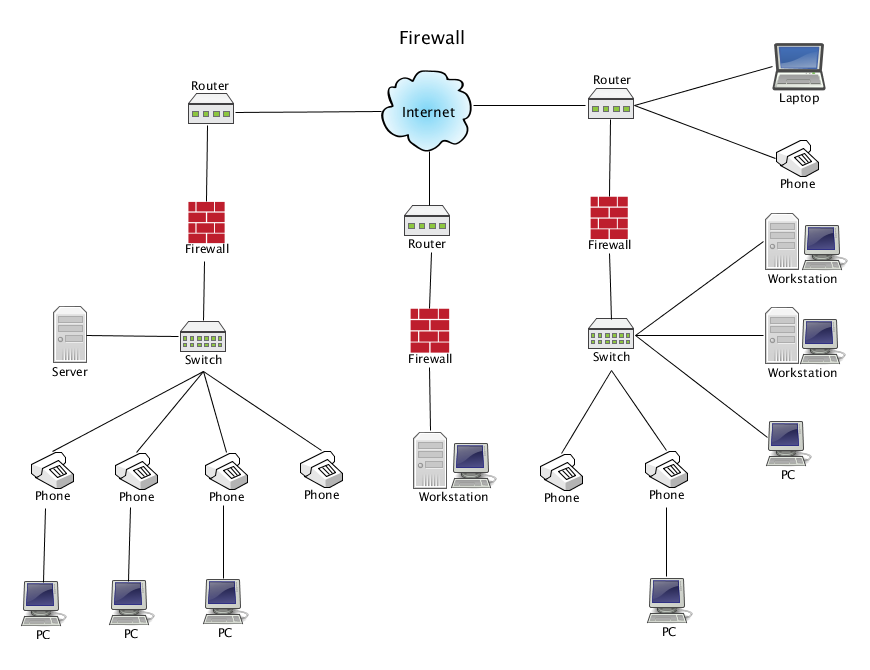
How To Use RemoteIoT Behind Firewall Using Mac Server Example
In today's interconnected world, managing IoT devices behind a firewall has become a critical challenge for businesses and tech enthusiasts alike. The ability to securely access and manage these devices remotely is essential for maintaining efficiency and ensuring data security. Using a Mac server as an example, this article will guide you through the process of setting up and managing RemoteIoT systems behind a firewall, ensuring seamless communication without compromising security.
As more organizations adopt IoT technologies, the need for secure remote access has never been greater. Firewalls play a pivotal role in protecting sensitive data, but they can also create barriers for IoT devices that require external connectivity. By leveraging a Mac server, you can create a robust and secure environment that allows for remote IoT management while adhering to strict security protocols.
This guide will explore the best practices, tools, and configurations necessary to achieve this setup. Whether you're a network administrator or a tech-savvy individual, understanding how to use RemoteIoT behind a firewall is an invaluable skill in today's digital landscape.
Read also:Luca Swat The Rising Star In The World Of Entertainment
Table of Contents
- Introduction to RemoteIoT and Firewalls
- Why Use a Mac Server for RemoteIoT?
- Basic Setup of Mac Server
- Configuring Firewall Settings
- Securing IoT Devices Behind Firewalls
- Tools Needed for RemoteIoT Management
- Example Implementation on Mac Server
- Troubleshooting Common Issues
- Best Practices for RemoteIoT Management
- Future Trends in IoT and Firewall Management
Introduction to RemoteIoT and Firewalls
RemoteIoT refers to the ability to manage and control IoT devices from a remote location. This capability is crucial for maintaining operational efficiency and ensuring that IoT devices function optimally, even when they are not physically accessible. Firewalls, on the other hand, act as a barrier between internal networks and the external world, protecting sensitive data and preventing unauthorized access.
Understanding how to use RemoteIoT behind a firewall involves configuring your network settings to allow secure communication while maintaining the integrity of your firewall. This balance is essential for ensuring that IoT devices can be managed effectively without exposing them to potential security threats.
In this section, we will explore the fundamental concepts of RemoteIoT and firewalls, setting the stage for more detailed discussions on configuration and implementation.
Why Use a Mac Server for RemoteIoT?
Mac servers offer a unique combination of user-friendly interfaces and powerful capabilities that make them ideal for managing RemoteIoT systems. Apple's macOS provides robust security features, seamless integration with other Apple devices, and a stable platform for hosting IoT management services.
Advantages of Using a Mac Server
- Highly secure operating system with built-in firewall capabilities.
- Easy-to-use interface for configuring network settings.
- Compatibility with a wide range of IoT devices and protocols.
- Reliable performance and stability for long-term use.
By leveraging these advantages, Mac servers provide an excellent foundation for setting up and managing RemoteIoT systems behind firewalls.
Basic Setup of Mac Server
Before diving into the specifics of configuring your Mac server for RemoteIoT, it's essential to understand the basic setup process. This involves installing the necessary software, configuring network settings, and ensuring that your server is ready for IoT device management.
Read also:Faggot Meme A Comprehensive Analysis Of Its Origins Impact And Cultural Significance
Steps for Basic Setup
- Install macOS Server on your Mac.
- Set up a static IP address for your server.
- Enable remote management tools such as SSH and Remote Desktop.
- Configure network settings to allow secure connections.
These initial steps lay the groundwork for a secure and functional server environment, paving the way for more advanced configurations.
Configuring Firewall Settings
Firewall configuration is a critical component of setting up RemoteIoT behind a firewall. Properly configured firewalls ensure that only authorized traffic is allowed to pass through, protecting your IoT devices from potential threats.
Key Considerations for Firewall Configuration
- Identify the ports required for IoT device communication.
- Set up rules to allow specific IP addresses or networks.
- Enable logging to monitor incoming and outgoing traffic.
- Regularly update firewall rules to adapt to changing security needs.
By carefully configuring your firewall settings, you can create a secure environment that supports seamless IoT device management.
Securing IoT Devices Behind Firewalls
Securing IoT devices behind firewalls involves implementing multiple layers of protection to safeguard against unauthorized access and potential breaches. This includes using strong authentication methods, encrypting data transmissions, and regularly updating device firmware.
Best Practices for Securing IoT Devices
- Use strong, unique passwords for all IoT devices.
- Enable encryption for data transmissions between devices and the server.
- Regularly update device firmware to patch known vulnerabilities.
- Implement multi-factor authentication for added security.
These practices ensure that your IoT devices remain secure and protected, even when accessed remotely.
Tools Needed for RemoteIoT Management
Managing RemoteIoT systems requires the use of specialized tools that facilitate secure communication and efficient device management. These tools include network monitoring software, IoT management platforms, and security utilities.
Recommended Tools
- Network monitoring tools such as Wireshark.
- IoT management platforms like Home Assistant or OpenHAB.
- Security utilities such as Fail2Ban and ClamAV.
By leveraging these tools, you can gain greater control over your RemoteIoT setup and ensure that it operates smoothly and securely.
Example Implementation on Mac Server
To illustrate the process of setting up RemoteIoT behind a firewall using a Mac server, let's walk through a practical example. This example will cover the key steps involved in configuring your server and managing IoT devices securely.
Step-by-Step Guide
- Install macOS Server and configure basic settings.
- Set up firewall rules to allow IoT device communication.
- Install and configure an IoT management platform on the server.
- Connect IoT devices to the server and test remote access.
This example demonstrates how to create a functional RemoteIoT setup using a Mac server, providing a clear roadmap for implementation.
Troubleshooting Common Issues
Even with careful planning and configuration, issues can arise when setting up RemoteIoT behind a firewall. Common problems include connectivity issues, security breaches, and device malfunctions. Addressing these issues promptly is essential for maintaining a stable and secure system.
Tips for Troubleshooting
- Check firewall logs for signs of unauthorized access attempts.
- Verify network settings to ensure proper communication between devices.
- Update device firmware and server software to address known issues.
- Consult documentation and online resources for additional support.
By following these troubleshooting tips, you can quickly identify and resolve issues that may arise during the setup and operation of your RemoteIoT system.
Best Practices for RemoteIoT Management
Adhering to best practices is crucial for ensuring the success of your RemoteIoT setup. These practices encompass everything from secure configuration to regular maintenance, helping you maintain a robust and reliable system.
Key Best Practices
- Regularly review and update firewall rules to reflect changing security needs.
- Implement automated backups to safeguard critical data.
- Conduct periodic security audits to identify potential vulnerabilities.
- Stay informed about the latest trends and developments in IoT and firewall management.
By following these best practices, you can ensure that your RemoteIoT system remains secure and efficient over the long term.
Future Trends in IoT and Firewall Management
The field of IoT and firewall management is rapidly evolving, with new technologies and innovations emerging regularly. Staying informed about these trends is essential for maintaining a cutting-edge RemoteIoT setup that meets the needs of modern businesses and individuals.
Emerging Trends to Watch
- Advancements in AI-driven security solutions.
- Increased adoption of edge computing for IoT devices.
- Development of more secure communication protocols.
- Growing emphasis on privacy and data protection regulations.
By keeping an eye on these trends, you can position yourself at the forefront of IoT and firewall management, ensuring that your systems remain relevant and effective in the years to come.
Conclusion
In conclusion, setting up and managing RemoteIoT systems behind a firewall using a Mac server is a powerful solution for ensuring secure and efficient IoT device management. By following the steps outlined in this guide, you can create a robust and reliable setup that meets the needs of both businesses and individuals.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and network management. Together, let's continue to advance the field of remote IoT management and stay ahead of the curve in this ever-evolving landscape.